Appearance
OwlyScan Alerts Interface Guide
OwlyScan Alerts operates through a simple two-page interface. The system runs automated searches based on your company information and displays results in a straightforward workflow: first an overview of all alerts, then detailed analysis of specific findings.
Alert List Dashboard: Your Threat Intelligence Command Center
Upon logging into OwlyScan Alerts, you are presented with the Alert List Dashboard, which serves as your central command center for monitoring your organization's darknet exposure. This interface provides immediate visibility into all automated queries conducted on your behalf, enabling rapid assessment of your current threat landscape.
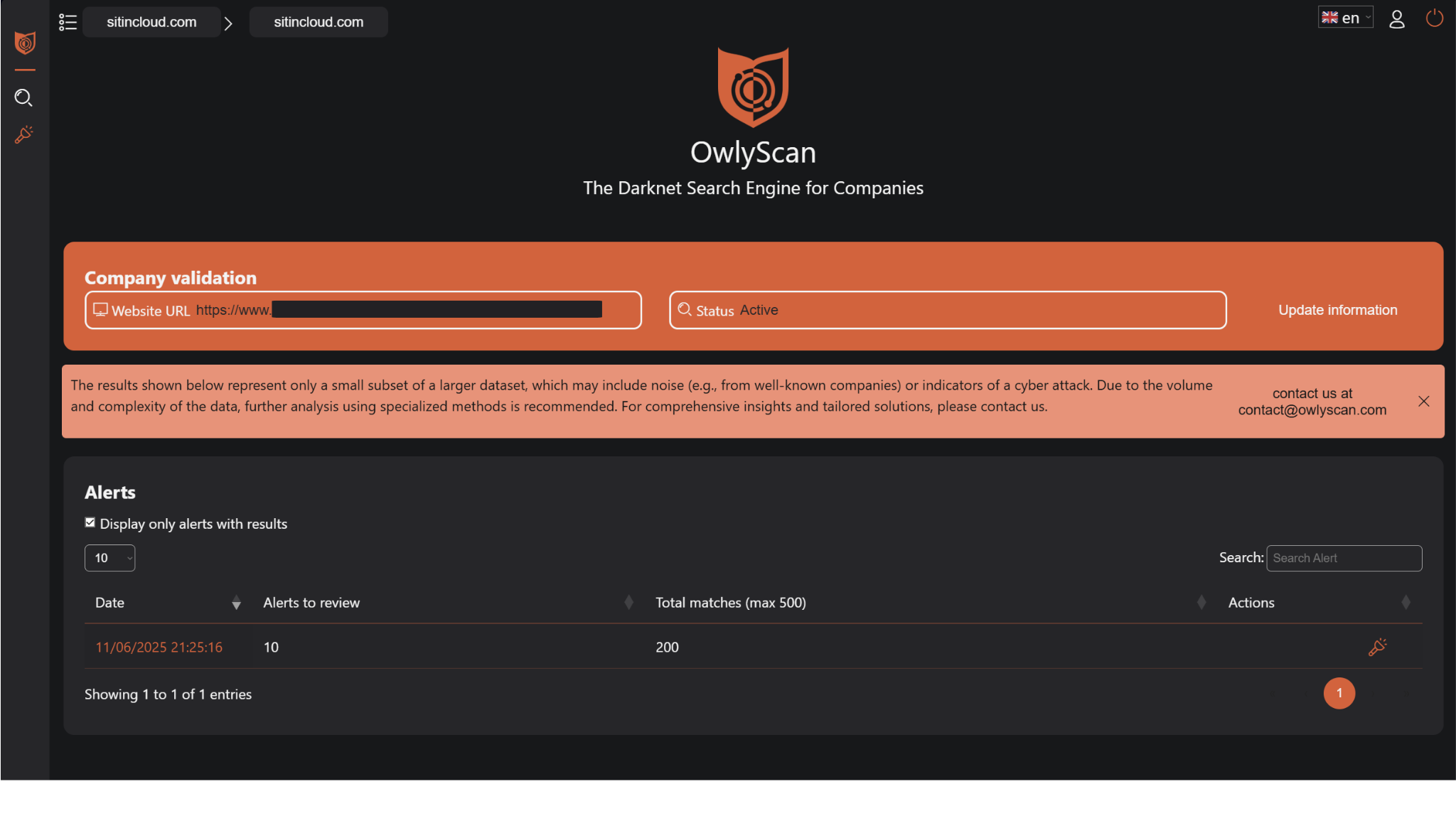
The Company Validation Header
The orange Company Validation header displays your organization's website URL, which plays a critical role in the intelligence gathering process. This URL serves as the primary reference point for OwlyScan's AI disambiguation system, helping the platform distinguish between documents genuinely related to your organization and those mentioning similarly named entities. This sophisticated filtering significantly reduces false positive alerts while ensuring comprehensive coverage of legitimate threats.
The status indicator confirms that your monitoring configuration is active and operating normally. The "Update information" option allows you to modify your organization's validation parameters when business changes require updated monitoring scope.
Understanding Your Alert Query Results
Below the validation header, you'll find an important notice explaining that the displayed results represent a carefully curated subset of a much larger dataset. OwlyScan's AI automatically processes hundreds of potential matches to identify the most relevant documents for your review. We acknowledges that this automated filtering, while sophisticated, may occasionally include noise from well-known companies or miss subtle indicators of cyber attacks.
Warning for big companies
For organizations requiring more comprehensive analysis or customized filtering approaches, direct consultation with OwlyScan's expert team is recommended.
The main alerts table presents a chronological list of all automated queries conducted for your organization. Each entry represents a complete intelligence gathering cycle, showing the date of execution, the number of alerts requiring review, and the total number of document matches discovered during that cycle.
The "Display only alerts with results" filter helps focus your attention on queries that discovered relevant intelligence, streamlining your review process by hiding empty searches. The search functionality enables rapid location of specific time periods or particular types of discoveries when you need to reference historical intelligence.
Each table row provides essential information for prioritizing your review efforts. The date column shows when each automated query was executed, providing temporal context for understanding the freshness of discovered threats. The " Alerts to review" column indicates how many distinct document groupings require your attention, while "Total matches" shows the comprehensive scope of materials discovered, capped at 500 documents per query cycle to ensure manageable review processes.
The actions column provides direct access to detailed analysis of each query's findings, enabling seamless navigation from overview to investigation.
Alert Details: Comprehensive Threat Analysis
Clicking on any alert entry navigates you to the Alert Details page, where OwlyScan presents comprehensive analysis of all materials discovered during that specific query cycle. This interface transforms raw darknet intelligence into actionable business intelligence through sophisticated categorization and presentation.
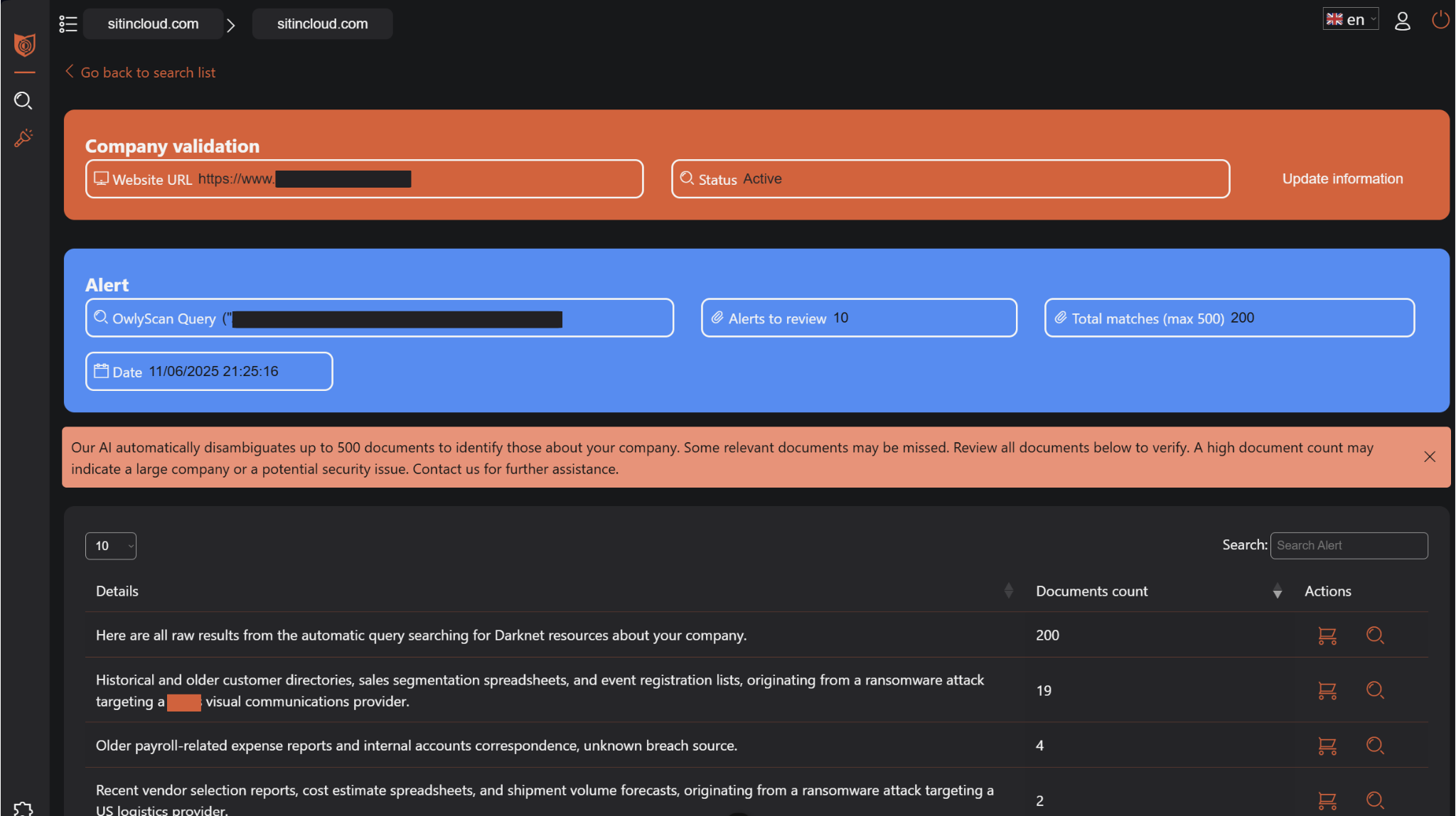
The Context Header
The blue Alert header provides immediate context about the automated search that generated these findings. The "OwlyScan Query" field displays the specific keywords and parameters used by the AI system to identify potentially relevant documents. These automatically generated search terms are derived from your organization's profile, industry context, and previous discovery patterns, ensuring that monitoring evolves to address emerging threat landscapes.
The header also shows the number of alerts requiring review and the total document count, providing immediate insight into the scope of analysis ahead. The date stamp ensures proper temporal context for assessing the urgency and relevance of discovered materials.
An important AI disambiguation notice explains that OwlyScan automatically processes up to 500 documents to identify those most relevant to your organization. This sophisticated filtering process helps distinguish between documents genuinely related to your business and those mentioning similar entities or common terms. The system acknowledges that some relevant documents may be missed due to the complexity of automated analysis, and encourages review of all findings to verify completeness.
The Document Analysis and Categorization Table
The main results table presents discovered documents organized by thematic groupings, enabling efficient review of related materials. Each row represents a cluster of documents sharing common characteristics, origins, or content themes, with the document count indicating the volume of materials in each category.
The "Details" column provides executive summaries of each document cluster, focusing on business impact rather than technical specifics. These AI-generated descriptions help executives quickly understand the nature of discovered materials, their potential origins, and their relevance to organizational security.
For example, the interface might present clusters such as "Historical and older customer directories, sales segmentation spreadsheets, and event registration lists, originating from a ransomware attack targeting a US visual communications provider." This type of description immediately conveys the business context, data types involved, likely compromise vector, and potential impact scope.
Additional categories might include "Older payroll-related expense reports and internal accounts correspondence, unknown breach source" or "Recent vendor selection reports, cost estimate spreadsheets, and shipment volume forecasts, originating from a ransomware attack targeting a US logistics provider." Each description provides sufficient context for executives to assess priority and determine appropriate response measures.
Response and Investigation Actions
Each document cluster provides two distinct action options, enabling appropriate response based on your organization's needs and available resources.
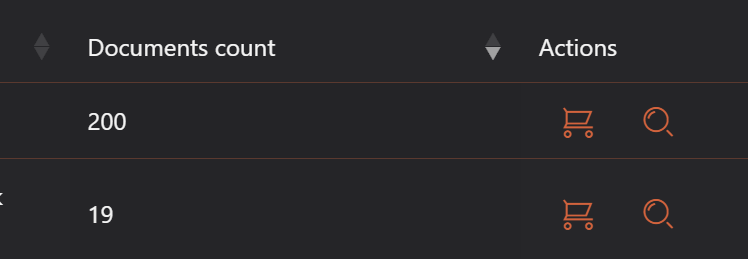
The first action button enables ordering a manual report from OwlyScan's Cyber Threat Intelligence (CTI) human experts. This premium service provides comprehensive analysis conducted by experienced threat intelligence professionals who assess the nature of discovered leaks, evaluate their potential danger to your organization, and provide specific recommendations for response and mitigation. Expert analysis proves particularly valuable when discovered materials involve sensitive business information, large-scale data exposures, or unclear threat attribution.
The magnifying glass button provides direct access to raw darknet resources, enabling technical teams to conduct detailed forensic analysis of discovered materials. This function displays actual document excerpts, file metadata, and precise darknet locations where materials were discovered, supporting comprehensive incident response and evidence collection requirements.
Raw Document Review Interface
When you click the magnifying glass to examine raw resources, OwlyScan presents the underlying darknet intelligence in a format suitable for technical analysis while maintaining appropriate security safeguards. This interface shows actual document excerpts, file locations on darknet sites, and contextual information about how and where materials were discovered.
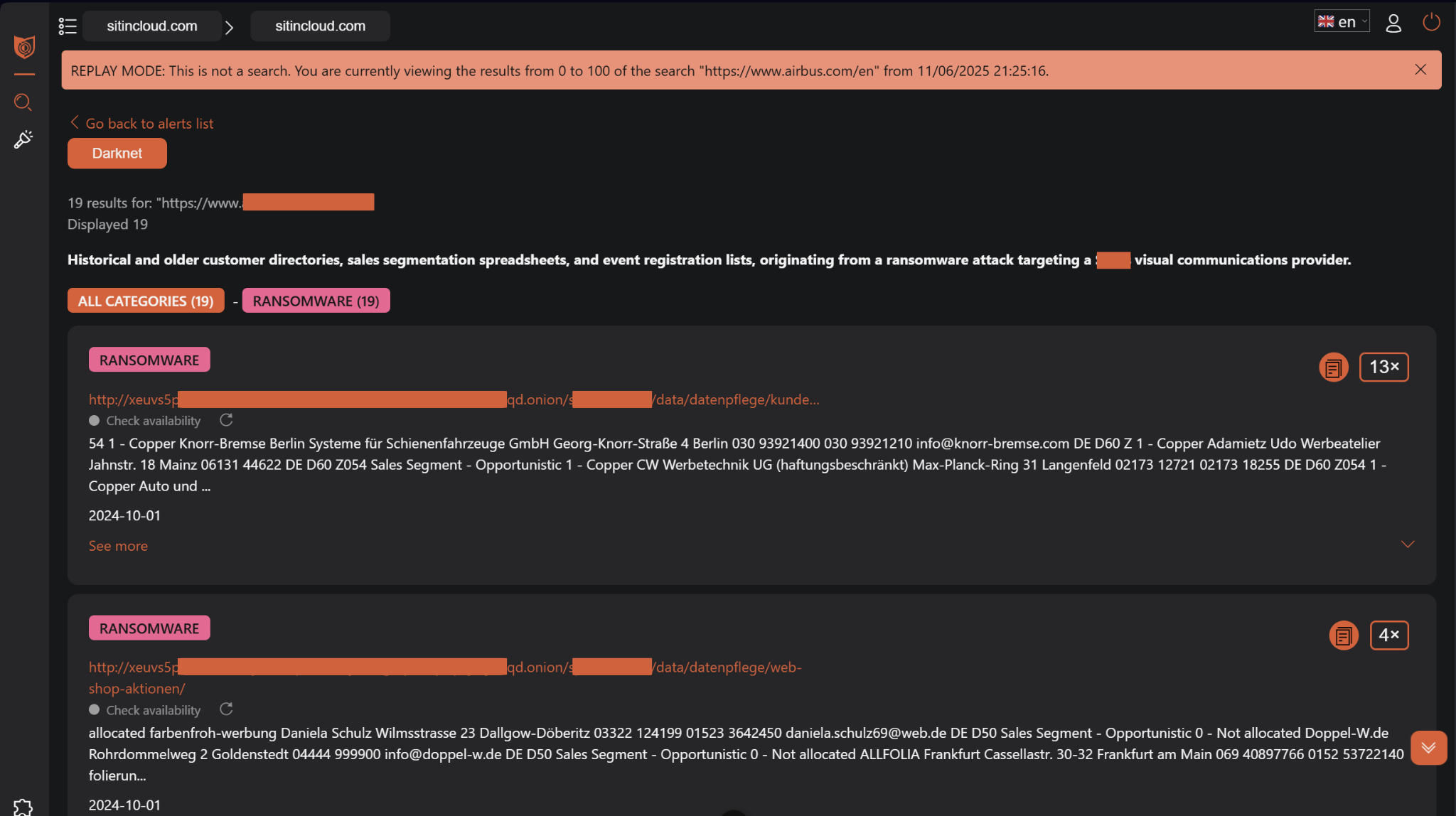
The raw document view maintains the security header showing your organization's validation context while presenting detailed findings. You'll see specific file types, discovery dates, and source contexts that help technical teams understand the scope and nature of each exposure.
Document excerpts provide sufficient detail for impact assessment while filtering potentially harmful or violent content. Each document entry includes metadata about its discovery source, enabling technical teams to understand the broader context of how your organization's information appeared in darknet sources.
The interface includes categorization tags such as "RANSOMWARE" or "FORUMS" to immediately identify the likely vector through which documents were exposed. This contextual information proves crucial for understanding whether exposures resulted from direct attacks on your organization or indirect exposure through partner breaches.
Workflow Integration and Response Planning
OwlyScan Alerts addresses three critical business security needs. First, it prevents spear phishing attacks by detecting when employee directories, organizational charts, or internal communications appear on darknet sources. Cybercriminals use this leaked information to craft highly targeted attacks against your personnel, making early detection essential for maintaining security awareness. Second, the service mitigates business risks by identifying when sensitive commercial information such as contract details, pricing data, or strategic documents are exposed. These leaks, often originating from compromised business partners rather than direct breaches, can provide competitors with valuable intelligence that affects your market position and negotiating power. Third, OwlyScan Alerts enables swift response during active cyberattacks by rapidly identifying what information has been compromised and where it appears on darknet sources. This immediate intelligence helps security teams understand the scope of an incident and prioritize their response efforts effectively.
Incident Response Support
If your organization becomes the victim of a cyberattack, OwlyScan can provide enhanced monitoring support by redirecting our crawling resources to prioritize the most relevant documents related to your incident. This focused approach helps you stay informed about new exposures as they appear, enabling you to act quickly and appropriately as the situation develops. To request priority monitoring during an active incident, please send an email to support@owlyscan.com with details about your situation and specific monitoring requirements.